
The US Department of Defense recently opened a new portfolio management office to help its agencies and commands accelerate the adoption of zero trust. Berenice Healey talks to Illumio about the principles of zero trust, the problems it solves and how best to implement it.
The zero trust security model applies the concept of “never trust, always verify” to the design of IT systems. Whereas traditional security measures trust devices within a corporate network, a zero trust architecture means devices are not trusted by default and should be individually authenticated regardless of physical location.
The US Department of Defence (DoD) setting up a portfolio management office (PMO) to support and fund zero trust programmes is a clear sign the principle has achieved legitimacy as a way of securing systems. Federal director at US business data centre and cloud computing security company Illumio Mark Sincevich explains why this is important.
Berenice Healey: In simple terms, what is zero trust architecture and why is it important within military circles?
Mark Sincevich: It works like security for a military forward operating base. With perimeter-based security, you decide you trust everybody; you say Mark wants to get into my network at the perimeter, he checks out so let him in.
Once I’m inside now I have free range at the military base. The problem with that is that if I have nefarious intentions, then I can go to the highly-available assets on the base and upload malware.
With zero trust you treat your assets like a secure compartmentalised information facility, or SCIF, rather than a forward operating base. It relates to how you would get into layers of security.
If I want to get in, you go to a highly-classified command centre, you first go through the perimeter security of the military base. Then you have the security at the front desk of that particular building and then additional security at the door into the command centre. That’s compartmentalisation or segmentation.
That’s what you do on a network; segment it so I can’t have free rein. The problem without zero trust is you get inside of the network and then somebody just walks around. These unrestricted packets go right to the high-value assets.
Zero trust means don’t trust anybody, and only trust those people that are highly verified for those packets or those workloads and make sure that you constantly challenge them. It’s not enough to say Mark can get in from the outside to the inside of the perimeter and always gets checked. Now he is going to be constantly asked where’s your pass at each segment and area. That’s outside in.
One of the pillars of zero trust is identity management. I access an application that’s outside in. The software will ask does Mark have the ability to access Excel, for example. Unbeknownst to me, that Excel application is now going out to a database to retrieve information and maybe doing something with another service. That’s a massive attack vector for moderate- to highly-sophisticated cyber attackers.
We take care of the inside-out approach, and you need both. I have a policy that says this Excel application can only talk to this workload and this database. Then if an attacker tries to get in, they will never be able to get the data because the policy is outside. And it’s quite brilliant actually, about what they’re able to do.
How does the zero-trust approach work for a military customer?
Most federal agencies and commands are very focused on devices and the network itself. When you talk to somebody who knows networking, you say, are you doing segmentation or even micro-segmentation? They’ll say, yeah, we’re doing that from a networking perspective.
The problem with that is that’s based on network security constructs. We have to go to the other side of zero and to the applications and workloads pillar of zero trust.
Everyone knows the military concept of prioritise and execute; you can’t do everything well, you have to do one thing well, and then prioritise the rest. And the problem now is that folks are focusing on the right-hand side of the blue line.
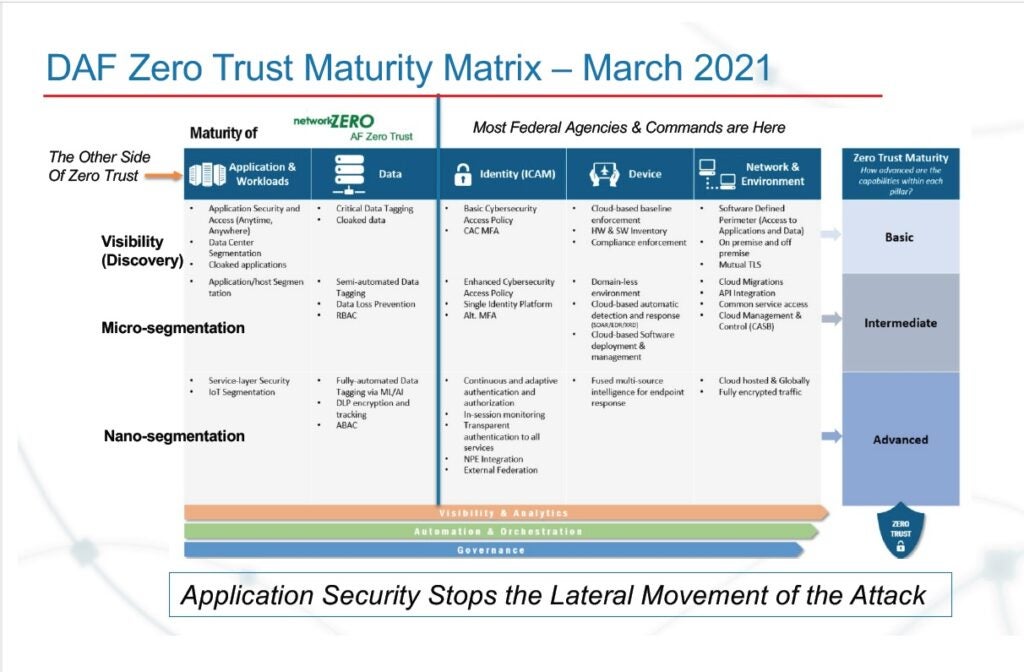
I will tell you right now with 100% certainty that next SolarWinds attack, none of these things are going to prevent that attack because you have to go to the application workloads pillar of zero trust and you have to go to micro-segmentation. We call this post-based micro-segmentation, which means we tap into the native stateful firewall of each one of the assets whether it’s hardware or software, right the operating system.
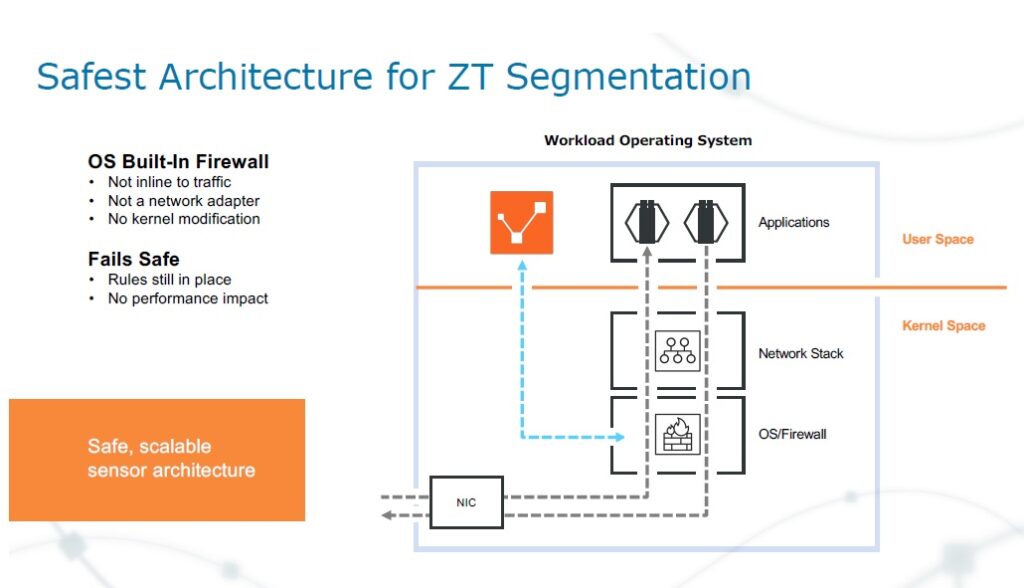
This shows the safest architecture for zero trust segmentation. Every other network segmentation is dependent on network security, it’s part of the network stack. If your network architecture is in flux, or has changed it’s going to be a problem, because you can’t segment quickly. We sit in user space and bypass the network stack because we’re focused on application security and go right to the native stateful firewall.
We put our software into one of the Patrick US Space Force B, home of Space Launch Delta 45. Within 10 minutes of us putting our software on their classified network, they were able to see unauthorised connections. They were like, whoa, we had no idea that we had those, so they shut them down immediately.
Then they started to bring in micro-segmentation and vulnerability data. Let’s say that you have port 443, which is highly vulnerable and it’s a score of 85. Using prioritise and execute we can then lock that down, then we can go down the list and start to microsegment and we have reduced the attack vector significantly. Now we can start to roll out a micro-segmentation strategy that will take not years, not months, probably a week or two depending on the size of the workload.
The DoD is launching a new zero trust portfolio management office. Why has zero trust become so important for defence now?
The cyberspace lab report came out in March 2020, which said that the USA is dangerously unsecure in cyber. The problem is we can’t defend forward if you have to keep looking over our shoulder. Based on that report and work with the DoD, they came out in February of 2021 with a zero-trust reference architecture.
This was a good first attempt; they specifically called out micro-segmentation. The foundation of the house is NIST 807, a reference architecture document the DoD created. Illumio is called out in that document where they specifically talk about host-based micro-segmentation.
The question is, why is this happening right now? A few commands and agencies are going in on their own and they have a little bit of a different approach. It takes a long time to sort out what works and we’re losing time.
One of the reasons this office was created is similar to why the US Office of Director of National Intelligence was created in some respects, to oversee all the 16 other US intelligence agencies and offer continuity. When the DoD creates a PMO, that means it has funding attached to it and to have an understanding of what’s going on.
Do you have recommendations on implementing zero trust?
The number one thing that I’d recommend is to set up the zero trust task force to ensure you have accountability and make sure it has funding.
Number two is to have innovation and collaboration centres, right. We went to Hanscom Air Force Base, which is right outside of Boston, Massachusetts and did a week-long, high-value asset exercise, otherwise known as a red team.
We trained 52 airmen and guardians for two days on Illumio. Then we set up exercises conducted by elements of the Army National Guard 126 Cyber Protection Battalion. and those guys tried to break in and get through the Illumio policy they did not do it after multiple attempts. That exercise alone in and of itself allowed us to go to work with the Department of Air Force on micro-segmentation.




