These days, any business that deals with sensitive information should be taking appropriate measures to protect itself from corporate espionage, particularly when many are now working as a remote workforce that may lack the security of an office environment.
According to David Vollmar, managing director at security innovator unival group, integrating counter-surveillance with your business’s global security policy has never been more important: “Typically, counter surveillance or TSCM is considered as a separate domain, but this credo has to change. The structure of how information can be acquired has become so broad that it really needs to be natively integrated with the security policy and made a part of standard security routines.”
Suspect signals
There are myriad ways information can be lost. Whilst identifying every kind of threat can be difficult, implementing a policy that incorporates physical security, cyber security and protection from electronic surveillance can help to protect against a sensitive information leak.
One classic form of electronic espionage, for example, is for an outside player to tap into a business call. Preventative measures include a regular bug sweep to seek out active devices, but bugs are often able to evade these sweeps. Plus, in a modern business environment there can be any number of transmitters, making it difficult to locate a foreign device, particularly when modern surveillance technologies are also highly discreet.
In fact, even the smallest device can hold a considerable amount of technology. They can be integrated into USB cables, light bulbs or any number of other common objects and, when not in use, can be placed on low power stand-by.
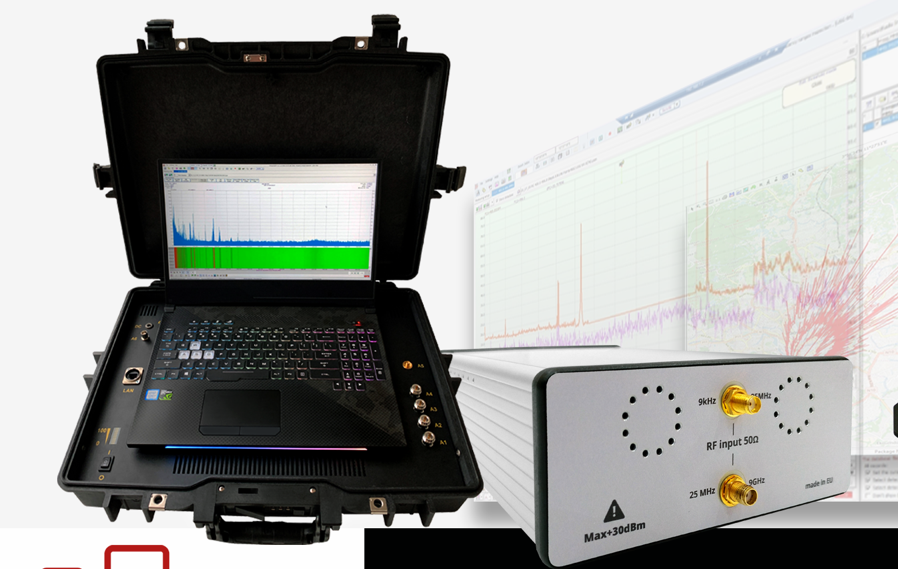
According to unival, the best way to provide complete assurance against these threats is with counter-surveillance equipment such as a continuous real-time in-place monitoring system. unival’s USG TSCM system offers round-the-clock guaranteed detection, continuously monitoring the environment to instantly detect suspect signals in real time. Even if a device transmits for less than a second, the unival USG will detect it. As a big benefit, the USG series can also act as a Counter-UAS monitoring system, allowing organisations to detect any suspicious drone activities in order to understand if they need to install permanent effectors, which unival group offers and can integrate seamlessly.
Counter-surveillance and Covid
Of course, physical electronic eavesdropping is not the only method of corporate surveillance. Cybersecurity has never been a more important component of a company’s security policy, particularly with Covid making remote working the new normal.
“Firewalls and IT security have become relatively sophisticated,” says Vollmar. “This means that hackers require specific information about staff or a particular person in order to make sure that they will open a compromising email. Often, information which was obtained using a bug that has eavesdropped on a call for example, will then be used – especially for more sophisticated attacks – to create a custom Trojan or any kind of vulnerability, to penetrate the system.”
This overlap between electronic and cyber surveillance highlights the need for a robust security strategy that straddles all avenues of information leaks. “It’s very important to control both measures and to synchronise these efforts,” says Vollmar. “A lot of organisations have been overwhelmed with enabling a mobile workforce over the last year, and they are slowly starting to adapt to this. They are now identifying that to prevent this kind of information loss, these threats will need to be a significant consideration in the coming months and years.
“It means it will be essential to have chief security officers with a broad knowledge across different areas, including an understanding of the threats coming from the cyber spectrum and all other routes of potentially harmful activity.”
A holistic approach
In addition to having the right personnel and a robust security strategy, implementing highly effective counter-surveillance equipment is also essential. “At unival, we provide solutions across the whole spectrum,” says Vollmar. “From screening devices and counter-monitoring equipment, to physical security. We work as an integrator, and this allows us to create a unique solution which is catered to the client’s specific requirements.
“We look at security from a holistic point of view, because we understand that access, counter-monitoring, video surveillance, and all other measures have to be considered in order to provide the strongest type of protection against threats to your organisation.”


