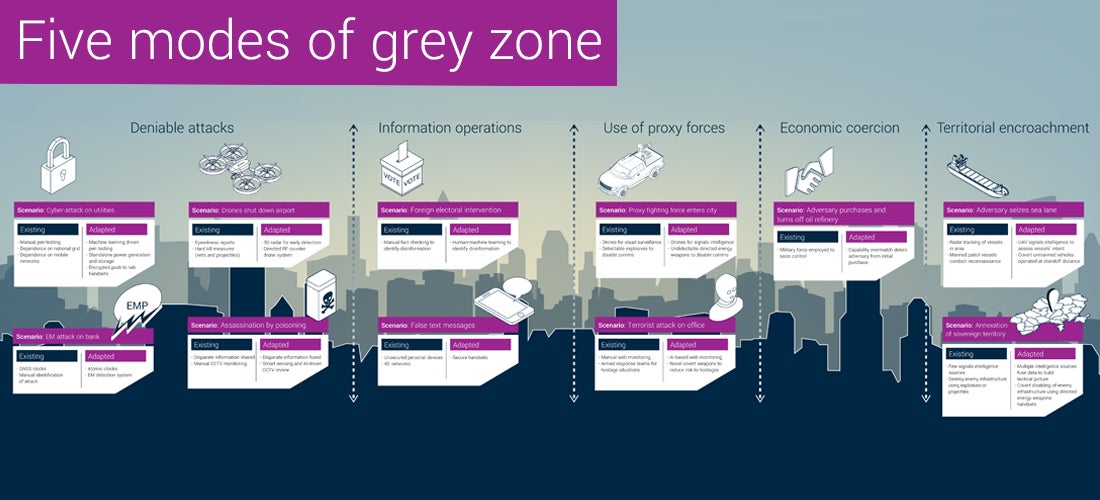
The landscape of global warfare is experiencing the next seismic shift in its history. The technological developments of the 20th and 21st centuries contributed to the development of well-trained and equipped armies across the world, a departure from that privilege being held by only the richest nations. Now, as the democratisation of technology advances, it is no longer just countries with huge spending power that can arm themselves with weapons of warfare – it can now be done on an individual basis too.
These weapons of warfare are not the conventional rifle or tank, but rather non-unique computers which through expert use give bad actors the ability to inflict damage on their targets, whether they be governments or proxies of government. Action in this way is now understood to take place within the grey zone – an area in which bad actors are able to attack political, economic and military instruments without provoking a conventional response, or even being recognised as formal acts of aggression.
The increasing relevance of the grey zone is demonstrated by the number of acts within it making the news. Whether it be attacks by Russian hackers against the Tokyo Olympics to cause disruption or GCHQ employing an offensive cyber-operation to disrupt attempts by hostile states to spread anti-vaccine propaganda, the grey zone is quickly becoming a major area of growth within warfare. The accelerating transfer of consumer technology from lab to user continues to lower the bar for entry and we’re likely to see an increased number of those with the capabilities to act within the grey zone.
A shared problem
As often is the case with warfare, its boundaries can often be blurred, and private parties can find themselves falling victim to acts of warfare, particularly within the grey zone. A combination of a lack of defined lines of battle and unconventional weapons, means acts involve much less overt conflict. In many cases, we see subtle measures put in place to disseminate misinformation on mass – which in turn causes the degradation of confidence in a government – the ultimate desired outcome for adversaries.
Consequently, it becomes very easy for grey zone attacks to spill over into the private sector. The current global pandemic in which we find ourselves provides ample opportunity. An adversary wanting to destabilise a government, and cause significant reputational harm, could target and derail their Covid-19 testing regime. In a UK context, this would mean targeting one of the private companies that have won the contract to administer it. That company now has the responsibility of addressing that attack, whilst the government and society also suffer harm. Another avenue for bad actors could be to disrupt the UK’s privately managed power and broadband services or meddle with its transport and signalling infrastructure. Suddenly, dozens of organisations – many of whom might not even be directly in the supply chain to the government – are potentially at risk.
What needs to be done
Fortunately, a shared problem can be met with a shared approach. Those on both sides of the public and private divide can work together to strengthen defences. For those private organisations, here are three key steps:
- Evaluate and understand your risk: As is evident from the current news cycle, cyber-attacks are becoming increasingly a weapon of choice for those conducting organised crime. With more and more software businesses within the market, whether focussed on accounting or project management, attackers have more avenues to penetrate unwitting end-users. This issue has been compounded by the unavoidable growth in remote working, forcing a migration to the cloud. With a technology framework so fragmented it is difficult to maintain resilience, that’s why an understanding of where potential weak points are is integral to a defence.
- Enhance your awareness: As the range of threats become more varied, they also become harder to identify. A key component of resilience is early detection. Chief Information Security Officers (CISOs) need to have an understanding of which unconventional tactics could be at play and know when and how to act. With an evolving threat, gaining that awareness requires proactive decisions and making sure everyone in the company is aware of how to report suspicious activity and the process to follow. Companies may therefore wish to seek out training from experts such as white hat hackers, or recruit those with a skillset capable of countering the ever-evolving tactics of bad actors.
- Build in new resilience measures: Whilst there is a growing number of threats from the democratisation of technology, there is also a growing use of it as a defence; in this case, artificial intelligence (AI). In the wrong hands, it can be used as a powerful weapon, capable of uncovering and exploiting vulnerabilities the human eye cannot find. However, as a tool in defence, its ability to process huge volumes of information simultaneously make it a key weapon within a defensive armoury. For CISOs, knowledge is power when it comes to developing a resilient framework and AI makes garnering that knowledge much easier.
Final thoughts
There is no sign of the grey zone’s growth slowing. The availability of complex technologies to consumers will continue to rise and with it, the capabilities of individual bad actors taking advantage of the benefits they offer, consequently increasing the potential vulnerabilities businesses may have. It is important that CISOs acknowledge that this is not just an issue for their country’s defence organisations, but that they are just as much at risk of being caught in the crossfire and likely to face significant impacts – both financial and reputational. Now is the time to critically assess security frameworks, and where necessary work to build in solutions which can ensure resilience in the long-term.

Image: QinetiQ senior business development manager Mike Tagima.